A 2023 review on the SANS SEC504: Hacker Tools, Techniques, and Incident Handling + GCIH Exam: what to expect and how to ace the GCIH exam.
I recently had the privilege to take the SANS SEC504: Hacker Tools, Techniques, and Incident Handling (SEC504) OnDemand training course taught by SANS Fellow and Course Author Joshua Wright. I managed to achieve a score of 98% on the GIAC Certified Incident Handler (GCIH) exam and I’m here to share my thoughts on the course and some tips on acing the GCIH exam.
Why SEC504?
I came into this course looking to expand my knowledge of incident handling/response (IR) processes, and what really attracted me was the course outline which highlighted that SEC504 covers not only the typical IR processes (host/network/log analysis), but also covers the processes and best practices for effective Cloud IR, and how to leverage both industry-standard tools and the command line to perform IR.
The course covers the common hacking tools used in cybersecurity incidents, and how malicious actors utilize those tools to scan, compromise, pivot, and establish persistence in your systems. SEC504 also teaches participants how to identify and investigate the trails left behind by hacking tools, and how pivoting off those findings can uncover more threats in your environment to ensure a comprehensive and robust IR process.
In this post, I will share notes and highlight key takeaways from each section of the SEC504 course, my experience with the GCIH exam, and some tips for acing the GCIH exam (and GIAC exams in general).
The SANS SEC504 Experience
The SEC504 OnDemand course comes with the following:
- >20 hours of video recordings covering the course materials
- A total of 8 physical books, consisting of 5 books of course materials, 2 workbooks, and 1 CTF book
- Electronic copies of the course materials and workbooks
- MP3 audio files of the entire course
- 2 Virtual Machines containing the lab exercises and video walkthroughs for all the lab exercises
Purchasing a SANS OnDemand course provides you with 3 months of access to the video recordings and to download the electronic copies of the course materials and workbooks, MP3 audio files, and the 2 VMs – you can keep the materials forever after downloading them.
SANS also very kindly provides cheatsheets for most of the tools covered in GIAC exams, most of which can be found here. The CTF component (book 6) is not necessary for attempting the GCIH exam but a good way to practice the skills you learn during the course. Generally speaking, I needed one day to complete each section of the course and their associated lab exercises (5 sections = 5 days, ~8hours/day).
SEC504.1: Incident Response and Cyber Investigations
If you are relatively new to professional incident response and cyber investigations work, there is a lot (a lot) of content covered in this section, both in the theory and practical aspects. This section covers how to develop and build an IR process, practical IR for host, network, memory, and malware investigations, and my personal favourite, cloud investigations. It also contains materials for the command-line Olympics, allowing participants to practice Linux Shell commands and Windows PowerShell cmdlets that will be tested during the GCIH exam.
By the end of this section, you should know the phases of IR, and how to perform IR across different systems. There are 7 lab exercises (2 of which are optional) associated with this section.
Notes for 504.1:
- Incident Response
- 6-step Incident Response process (PICERL) and the Dynamic Approach to Incident Response (DAIR)
- Live Examination
- Areas to investigate for a Live Windows Host (Identifying and examining suspicious processes, network usage, local accounts, Registry keys etc.)
- Operating and understanding the Sysinternals suite of tools (procmon, procdump, sysmon, autoruns etc.)
- Network Investigation
- The sources of network information and the challenges associated with network investigations
- Understanding web proxies and reading access logs
- Using tcpdump (and Berkely Packet Filters) to manipulate packet captures
- Memory Investigation
- How to capture RAM images
- How to analyze RAM images using Volatility 3
- Malware Investigation
- Using online tools such as VirusTotal and Hybrid Analysis to automate malware analysis
- Differences in snapshot and continuous recording tools such as Regshot and Procmon
- Code disassemblers, debuggers, and decompilers
- Cloud Investigation
- Differences (and similarities) between on-premises and cloud IR
- Demarcation of security responsibility between cloud services (IaasS vs PaaS vs SaaS)
- Different logging types (API Access, network flow etc.), tools to ingest and analyze logs
Key Takeaways for 504.1:
- This section (and the course as a whole) places a huge emphasis on Windows PowerShell cmdlets to perform investigations Spend time on the Linux and PowerShell Olympics materials to familiarize yourself with using a command-line interface and learn commonly used commands. Throughout the rest of the course, you are expected to chain multiple PowerShell cmdlets to achieve your aims.
- Get familiar with the various Volatility 3 plugins and understand how to read their output.
SEC504.2: Recon, Scanning, and Enumeration Attacks
This section covers the tools and techniques attackers use for reconnaissance, scanning, and enumeration of a target. It also highlights the different type of intelligence that can be obtained from OSINT sources versus interacting with a target directly (scanning), and the value of the intelligence obtained. While the section covers how to use tools such as SpiderFoot and nmap, it also teaches about the trails left behind by such tools and how defenders can identify and investigate them.
By the end of this section, you should be able to explain how attackers gather information prior to an attack, and how to detect and mitigate them. There are 6 lab exercises associated with this section.
Notes for 504.2:
- MITRE ATT&CK Framework
- How the ATT&CK Framework maps to real adversary tactics, techniques, and procedures (TTPs) to give insights into how attackers operate and how subsequent sections in the course defend against these TTPs
- Open-Source Intelligence
- What is OSINT (and what is not), what kinds of OSINT are available, what to collect, where to look
- WHOIS information, certificate transparency searches using crt.sh
- Automating the OSINT collection process using SpiderFoot
- DNS Interrogation
- DNS record types and zone transfers using dig and nmap
- Best practices for DNS setup and logging for defense
- Website Reconnaissance
- Website crawling and wordlist generation using CeWL
- Google Dorks (and the Google Hacking Database)
- Public databases and sources of OSINT
- Using Internet scanning webpages (shodan.io, network-tools.com)
- Limiting data disclosure for defense
- Network and Host Scanning with Nmap
- Host discovery and enumeration using Nmap and the Nmap scripting engine scripts
- IP packet headers (IPv4 and IPv6) and how traceroute works
- Cloud Spotlight: Cloud Scanning
- Using JSON Query (JQ) to manipulate JSON data
- Cloud enumeration techniques for different cloud providers (GCP, AWS, and Azure) using Masscan
- Cloud host attribution using TLS-Scan
- EyeWitness to automate screenshots of websites and services
- SMB Security
- Security features across SMB versions
- Identifying SMB shares and enumerating files using SMBeagle
- Interacting with SMB using smbclient and rpcclient
- SMB exploits and attacks
- Defense Spotlight: DeepBlueCLI
- Parsing Windows event logs with DeepBlueCLI to analyze events and identify potentially malicious activity
Key Takeaways for 504.2:
- Know what is OSINT and what is not.
- Get comfortable with Nmap and take advantage of its wide range of capabilities.
- Understand the different enumeration techniques for cloud hosts and the tools that attackers use.
- This section (again) leverages many powerful PowerShell cmdlets that can be used to interact with SMB.
SEC504.3: Password and Access Attacks
This section extensively covers methods to identify and mitigate password and access attacks. It also focuses heavily on cloud enumeration and access attacks, which was a personal favourite of mine.
By the end of this section, you should be able to explain how attackers perform password attacks, and how to identify and mitigate them. You should also be able to explain the functionalities of Netcat. There are 6 lab exercises associated with this section.
Notes for 504.3:
- Password Attacks
- Understanding the differences between password guessing, spraying, and credential stuffing, and the mitigations in place to defend against these attacks
- Cloud Spotlight: Microsoft 365 Password Attacks
- Attackers can and will leverage cloud services to bypass mitigations and attack your cloud endpoints
- Understanding Password Hashes
- Weaknesses in legacy Windows password hashes that can be easily exploited
- Built-in tools can be used to obtain password hashes and are less likely to trigger alerts
- Modern password hashing algorithms like scrypt and Argon2 can slow down attackers considerably while having minimal impact on legitimate users
- Password Cracking
- John the Ripper and Hashcat can efficiently crack password hashes, especially if password policies or patterns are known
- Multi-Factor Authentication are essential to defend against most forms of password attacks
- Cloud Spotlight: Insecure Storage
- Attackers can enumerate cloud endpoints to identify your storage mechanisms and identify misconfigurations
- Misconfiguration in cloud storage can have devastating impacts
- Multi-purpose Netcat
- Netcat can be used to transfer files, perform port scanning, serve as backdoors, and act as relays for lateral movement
Key Takeaways for 504.3:
- Understand the different types password attacks against cloud and traditional systems, how they are carried out, how they can be detected, and how to mitigate them.
- Know the common hash types across Unix and Windows systems, and how to use John the Ripper and Hashcat to crack those hashes.
- Learn the ways attackers use Netcat to transfer data, setup backdoors, and perform lateral movement to target internal systems not typically reachable by external hosts.
SEC504.4: Public-Facing and Drive-By Attacks
This section focuses heavily on attacks on AND via public-facing systems, especially web applications. Participants who have a red-team background or have attended red-team courses are likely to breeze through this section. Personally, this section was more manageable for me as I have attended SEC560 and SEC542 in the past. That said, I felt more equipped to identify and mitigate such attacks after this section.
By the end of this section, you should be able to explain how attackers carry out attacks on/using public-facing systems, and how to identify and mitigate them. There are 7 lab exercises associated with this section.
Notes for 504.4:
- Metasploit Attack and Analysis
- Knowing the different Metasploit modules and when to use them
- Identifying Metasploit attacks using DeepBlueCLI
- Drive-By Attacks and the Browser Exploitation Framework (BeEF)
- Knowing the various attack vectors in watering hole and drive-by attacks
- Generating payloads with Metasploit MsfVenom
- Defense Spotlight: System Resource Usage Monitor
- Using SRUM-Dump to extract information from the SRUDB.dat file
- Manipulating SRUM-Dump output for analysis to identify malicious network activity
- Command Injection Attack
- Identifying, exploiting, and defending against Command Injection attacks
- Cross-Site Scripting (XSS) Attack
- Identifying, exploiting, and defending against XSS attacks
- Knowing the differences between stored and reflected XSS attacks
- SQL Injection (SQLi)
- Identifying, exploiting, and defending against SQLi attacks
- Using Sqlmap to automate SQLi identification and exploitation
- Cloud Spotlight: Server-Side Request Forgery (SSRF) and Instance Metadata Service (IMDS) Attack
- Identifying, exploiting and defending against SSRF and IMDS attacks
- Exploiting Local File Include vulnerabilities using SSRF
- Executing IMDS attacks for credential exfiltration
- Knowing the differences between IMDSv1 and IMDSv2
Key Takeaways for 504.4:
- Metasploit, Metasploit, Metasploit: Know the different Metasploit modules and their uses, how to search for them, and how defenders can identify attacks that utilize Metasploit.
- Know the similarities and differences between watering hole and drive-by attacks.
- Understand how to perform command injection, XSS, SQLi, and SSRF/IMDS attacks, and how to identify and mitigate them.
SEC504.5: Evasion and Post-Exploitation Attacks
Attackers do not stop after exploitation and defenders should be equally concerned about the objectives of attackers post-exploitation, and the steps attackers take to achieve their objectives. Not only does this section cover how attackers perform lateral movement and persistence, but also covers extensively on how defenders can identify and mitigate these tactics.
By the end of this section, you should be able to explain the objectives of attackers post-exploitation, and how to identify and mitigate the steps attackers take to achieve their objectives. There are 7 lab exercises (1 of which is optional) associated with this section.
Notes for 504.5:
- Endpoint Security Bypass
- Using DefenderCheck for avoid antivirus signature detection and code wrapping/obfuscation to bypass behavioral anomaly analysis systems
- Practicing the principles of Living Off the Land (LOL) to bypass security mechanisms
- Pivoting and Lateral Movement
- Performing pivoting using Meterpreter, SSH and netsh
- Hijacking Attacks
- Using Responder to target LLMNR protocol for hijacking attacks
- Establishing Persistence
- Different methods of persistence, covering Kerberos attacks, web-shells, backdoor accounts, and Windows Management Instrumentation (WMI) event subscriptions
- Defense Spotlight: Real Intelligence Threat Analytics
- Statistical analysis of events and network traffic using RITA to perform threat hunting
- Data Collection
- Data collection and exfiltration is often the ultimate goal of an attacker
- Ways to harvest Linux and Windows passwords with tools like Mimikatz
- Tackling password managers to harvest passwords using clipboard access
- Cloud Spotlight: Cloud Post-Exploitation
- Taking advantage of built-in cloud commands and tools for attackers to gain situational awareness
- Using Pacu and GCP PrivEsc to attack cloud services and perform privilege escalation
- Where to Go from Here
- Tips on long-term memory retention and how to pass the GCIH exam
Key Takeaways for 504.5:
- Attackers do not stop after exploitation; data collection and exfiltration are often the main objectives.
- Defenders should strictly control access to default applications, scripts, and binaries which can be abused for malicious purposes such as lateral movement and persistence.
The GIAC Certified Incident Handler (GCIH) Exam
The GCIH exam format is as follows:
- 1 proctored exam
- 106 questions
- 4-hour time limit
- A minimum passing score of 70%
- Open-book policy
Other key points to note about the exam format:
- The 106 questions consist of 96 Multiple-Choice Questions (MCQs) and 10 CyberLive questions (some have mentioned that there are 95 MCQs and 11 CyberLive questions)
- You are allowed to skip up to 10-15 questions during the exam; unanswered questions will be marked as “incorrect” at the end of the exam
- You are allowed to take up to 2 breaks for a combined total of 15 minutes during the exam
- You must answer any skipped questions before taking a break
- You are not allowed to revisit a question after answering it
- Practice exam questions will not show up in the actual exam
- You are only allowed written and printed materials in the actual exam; no electronic materials are allowed
Tips for the GCIH exam (and GIAC exams, in general)
Creating an index
If you have not heard of indexing, think of it as creating a personal directory consisting of important information that you may want to quickly access during your exam. As you are not allowed to bring any electronic materials into your exam, preparing a good index is essential – do not underestimate the amount of time you will spend flipping through your course materials when looking for information. While it is still useful, I do not recommend relying solely on the index provided by SANS (or someone else) as it has little contextual value to you.
For tips on creating an effective index, refer to Lesley Carhat’s pancake indexing strategy and devise a method that works for you. Personally, I color-code each book using visually distinct colors, and created my index using Microsoft Excel while going through the course materials. If creating an index while going through the course materials feels too disruptive, I know of other participants who only started on their index after completing the course materials. My index (keywords redacted) ended up looking something like this:
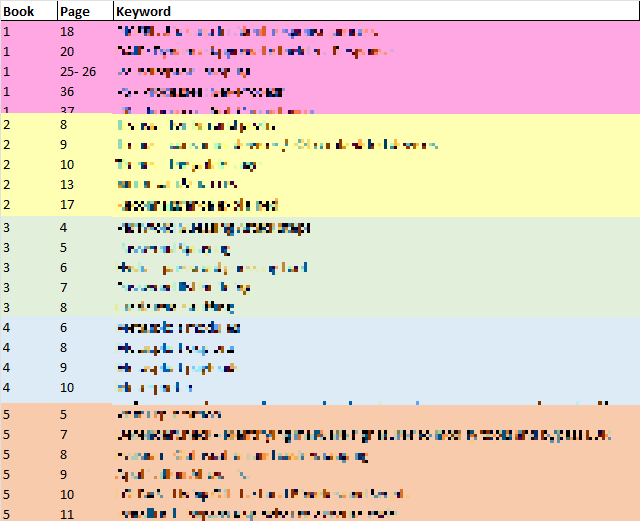
I then sorted it alphabetically based on the “Keyword” column so that it is in ascending order (A->Z).
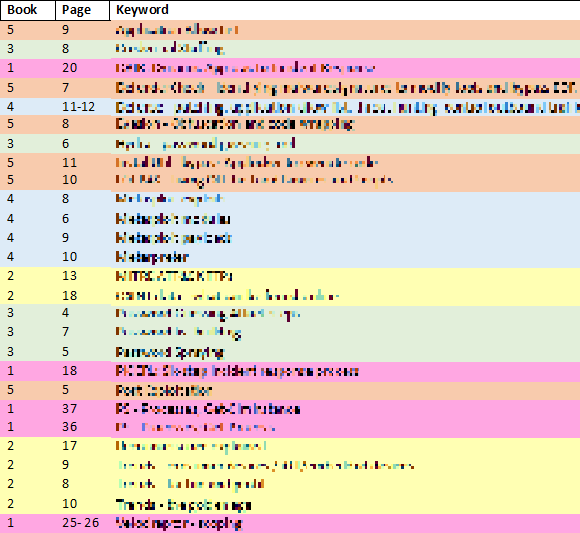
Once I was done with my index for GCIH, I had 220 rows of keywords. Feel free to include as many (or as little) keywords as you want. Remember – it is your index so it should make sense for you.
Time management
Time management is essential for the GCIH exam. I cannot stress how easy it is to underestimate the time needed to look for information in the course materials – there will not be enough time to flip through the course materials for every question. To recap, the exam consists of 95/96 MCQs and 10/11 CyberLive questions. I could not recall how many CyberLive questions I had to do, but assuming 10 CyberLive questions and keeping in mind a time limit of 4 hours (240 minutes), see the table below for how much time you can spend for each question:
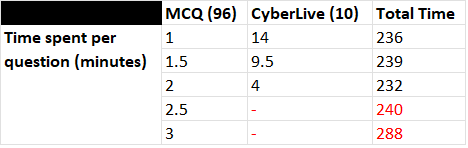
As you can see from the table above, every additional half-minute you spend on each MCQ will exponentially cut down on the time you have for the CyberLive component. If you consistently spend 2.5 minutes for each MCQ, you will not have any time for the CyberLive component. One of the most common reasons for running out of time is due to tunnel-visioning on questions that you are unsure of. To combat this, remember the two points:
- Skip questions if you are unsure – there are instances where I skipped 4-5 questions only to remember the answer later in the exam.
- Take advantage of the 15-minute break – a 4-hour exam is mentally and physically taxing. I found that taking a break around the 90-minute mark provided a welcome respite from the exam.
CyberLive
For participants who have not taken a GIAC exam with CyberLive questions before, it is essentially a VM in your browser. You are expected to utilize what you have learned in the SANS course to tackle CTF-style questions similar to your lab exercises. Based on my experience, the best way to prepare for the CyberLive component is to familiarize yourself with the lab exercises. You may be required to combine tools from different lab exercises to achieve your aims. Generally speaking, I would advise setting aside 5 minutes for each CyberLive question (a total of 50 minutes for 10 questions). My main gripe with CyberLive questions is that the VM in the browser can sometimes lag which can make it frustrating.
Practice Tests
Purchasing a SANS OnDemand bundle with a GIAC exam certification attempt also provides you with 2 practice tests. I highly recommend attempting at least 1 practice test (2 if possible) prior to the actual exam, especially if you have never attempted a GIAC certification before. These practice tests are in the same format as the actual GIAC exam, but they are not proctored. Treat the practice tests as if they were the real exam and utilize them wisely as they are the best indicator of how you will perform in the actual exam. Personally, I approached the 2 practice tests as such:
- Practice Test 1: Take your time to go through each and every question without worrying about speed and focusing on accuracy instead (keeping in mind the 4-hour time limit). Note down every question that you have doubts about, especially for the questions with answers that you felt were very similar. This practice test should accurately highlight the sections that you are uncertain about. Once you are finished with the practice test, take your time to polish up your index and look through the materials that you have doubts on. I would advise against taking 2 practice tests in the same day as it is unlikely that you can sufficiently digest the materials you revised.
- Practice Test 2: Attempt this practice test as if it were the real exam. Find a good pace to maintain your speed and confidence in answering questions. Get into the habit of skipping questions if necessary. Having taken 4 GIAC exams thus far, I found that my score for Practice Test 2 can accurately predict the final score on my exam, typically deviating only a few points from the actual final score. For reference, I scored 89% on Practice Test 1 and 93% on Practice Test 2.
Most importantly, if you are answer incorrectly, practice test questions will show you the correct answer, followed by an explanation on why that answer is correct!
Admission to GIAC Advisory Board
Participants who score more than 90% on their GIAC exams will be invited to join the GIAC Advisory Board, an invitation-only, email-based forum. It is also a way to demonstrate that you scored exceptionally well on your GIAC exams. My advice – study the course materials, get intimate with the lab exercises, and index.
Final Thoughts
It is no wonder the SANS SEC504 course the most popular SANS course ever – SEC504 presents a realistic and comprehensive overview on different attack vectors, how they are carried out and how incident handlers can confidently identify, defend, and remediate. In my opinion, this course is equally great for security analysts looking for hands-on experience on carrying out attacks as it is for red-teamers that want to understand how their attacks can be identified and mitigated. If you are taking the course in preparation for the GCIH exam, everything that you need to pass can be found in the course materials. The GCIH certification is great for cybersecurity professionals looking to acquire certifications due to the demand for it.
I hope this post helped to demystify the SANS SEC504 course and cleared any doubts you had about the GCIH exam. All the best!

Leave a Reply