Linking different scam series using OSINT
In our previous post, I covered how we can hunt for malicious APKs using Open-Source Intelligence (OSINT) and look for places where these APKs are hosted. These APKs were found to be banking trojans disguised as e-commerce applications and targeted victims via social media advertisements. Victims who installed the APKs and granted it permissions as an Android accessibility service subsequently had their phones taken over and bank accounts compromised.
In total, we found 14 malicious “1st Mall” APKs from Triage, 84 sites hosting the APKs from URLScan, and 26 newly registered domains potentially linked to the 1st Mall scam series.
In this post, I will build on the findings from the previous post and show how to link the “1st Mall” scam series to other scam series using OSINT.
Discovering related files with VirusTotal
VirusTotal is a malware analysis sandbox service that allows users to upload files and scan URLs with antivirus products (AVs). VirusTotal also has a impressive search and graph functions, allowing users to look for related files and map out their connections.
We will start with “1st Mall v11.1.apk” from the previous post to look for other related files.
After uploading the APK, the VirusTotal scan results show that the file was first analysed on 10 June 2023. The scan results show that 26 out of 64 AVs labelled the APK as malicious. Interestingly, the APK was tagged as a malware belonging to the spynote/spymax (spynote) family of malware. The other samples found from Triage also had similar VirusTotal results, with 20+ AV detections and were also tagged as a spynote malware.
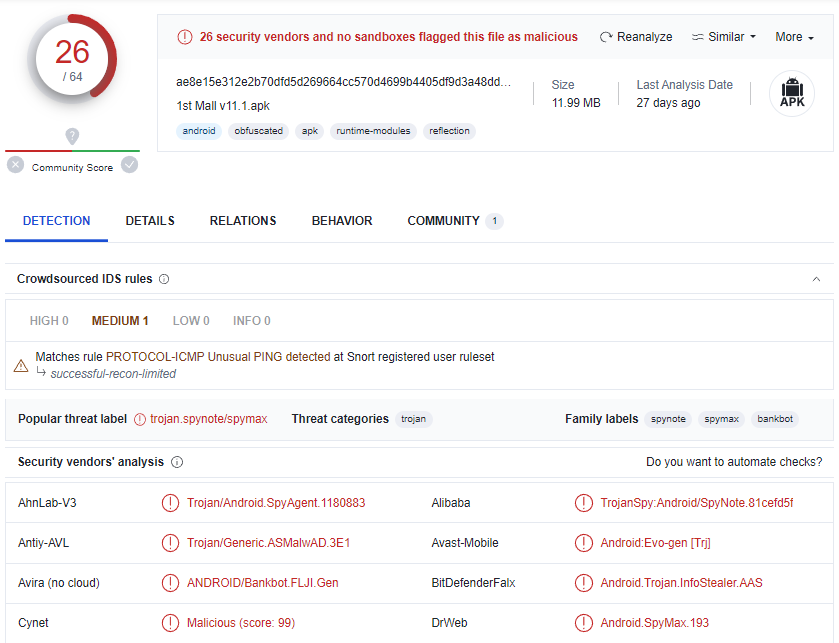
Reports of spynote malware can be found dating back to 2019 – you can read more about the technical details of the malware family here and here. In gist, after the malware is downloaded and installed, it downloads dex code from a C2 server whose IP address is hardcoded in the APK. The downloaded dex code contains additional functions for the malware operators, such as the ability to encrypt and upload files.
Back in VirusTotal, the “Relations” tab shows that the APK contacts the IP address “38.181.2.53“, identical to what was shown in Triage.
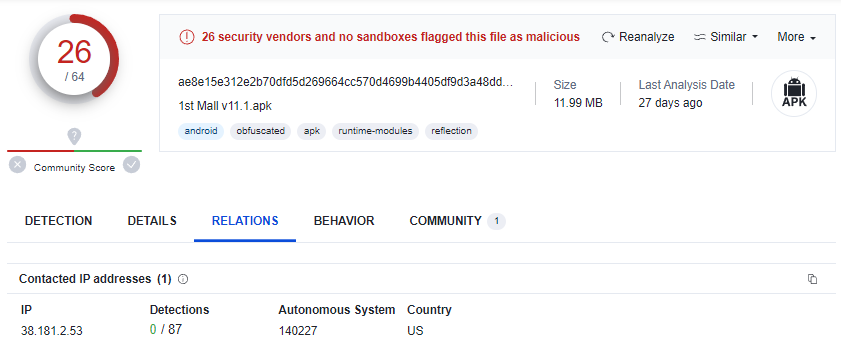
VirusTotal links indicators found across different files from user submissions. This helps us find other related files that are contacting the same C2, potentially uncovering other files used in scams. By clicking on the IP address, we are brought to the VirusTotal analysis of the IP address. From this analysis, the “Relations” tab reveals 14 other files found communicating with the IP address since June 2023.
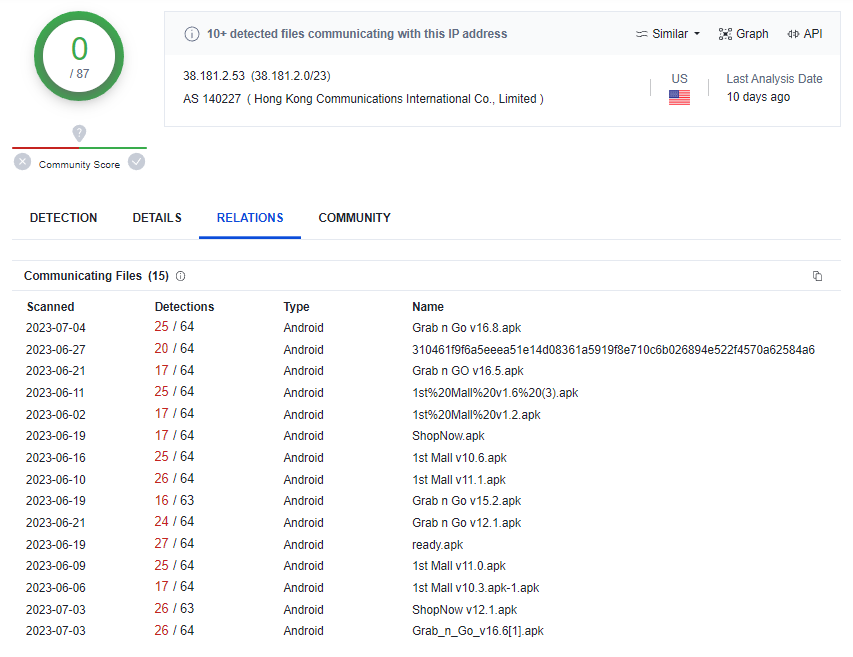
To recap, we detected 14 unique “1st Mall” APKs from our previous post with the following naming convention:
1st Mall v<major version number>.<minor version number>.apkFrom the analysis above, we see several other interesting APKs that bear a similar naming convention, such as “Grab n Go” and “ShopNow“. These APKs also have similar AV detection results and are all tagged as spynote malware.
Based on the similar naming convention of the communicating files, recency of information, and the fact that they all belong to the same malware family, it suggests that the operators of this C2 server could be concurrently running other scam series as well.
1st Mall to ShopNow to Deluxe Home?
In this section, we explore the other scam series by expanding on the second last communicating file from the previous screenshot.
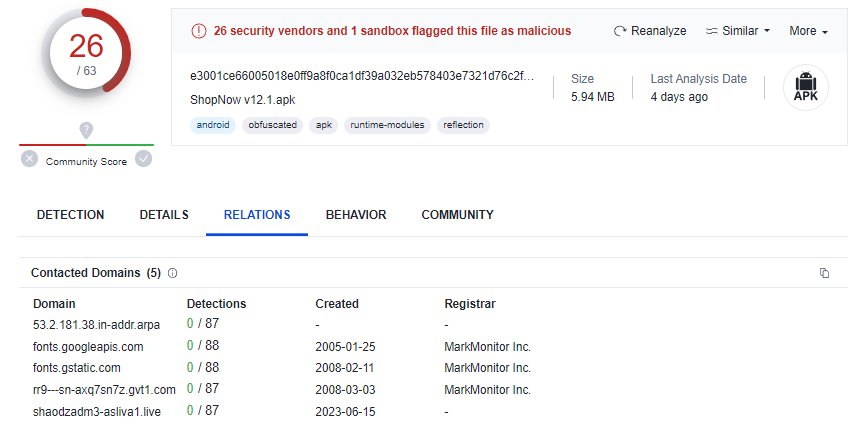
In the “Relations” tab of the “ShopNow v12.1.apk” analysis (second last communicating file), we see that the “ShopNow” APK was contacting the domain “shaodzadm3-asliva1.live“.
When browsing to the domain directly, I was met with an error stating that the site was blocked by my ISP. However, by changing my DNS server, the domain loads a WordPress site with e-commerce content.
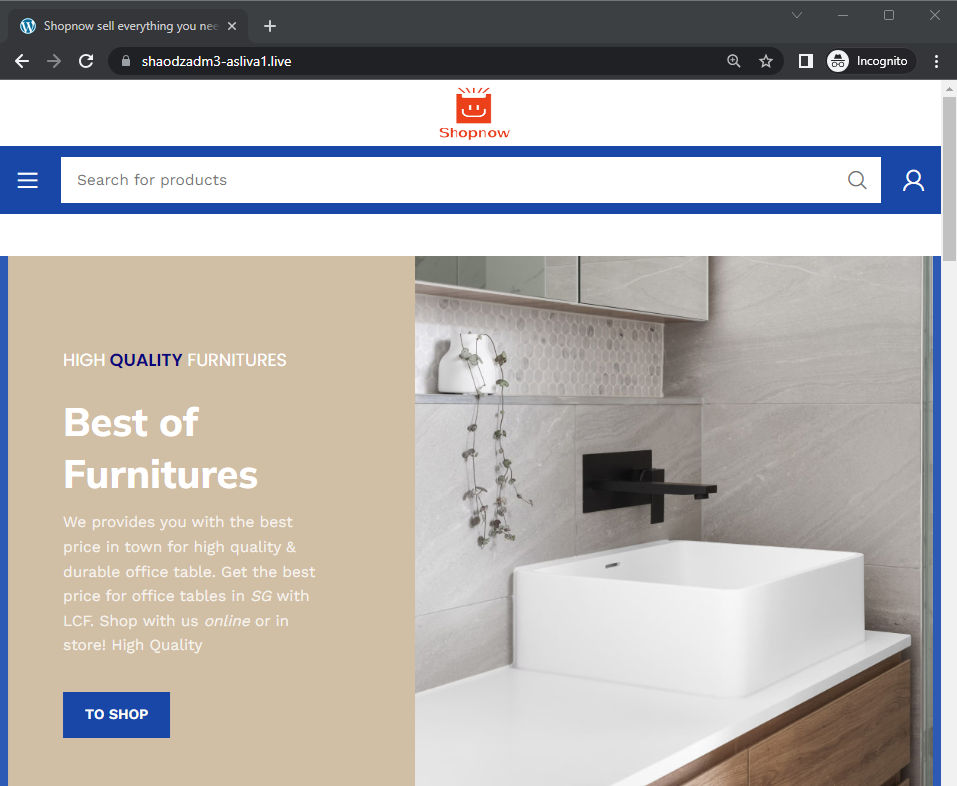
The site supposedly sells everything from furniture to cosmetic products to designer handbags for a fraction of their original price. The site also contains numerous broken links and placeholder text in item descriptions. All things considered, the site triggers a few alarm bells, and it is no wonder why the domain is blocked by my ISP.
The site’s HTML title is “Shopnow sell everything you need! – My WordPress Blog“, similar to the sites belonging to the “1st Mall” scam series.
Back at the VirusTotal analysis of the site, under the “Relations” tab, we see a Passive DNS result which resolved the domain to the IP address 103.99.60.82 on 17 June 2023. We also see another similarly named file, “Shopnow v18.0.apk”, communicating with the domain.

If we browse to 103.99.60.82:443 directly, we are shown an error that the SSL cert belongs to “https://fgeisdlwre3-yuzdersp9.top/“.
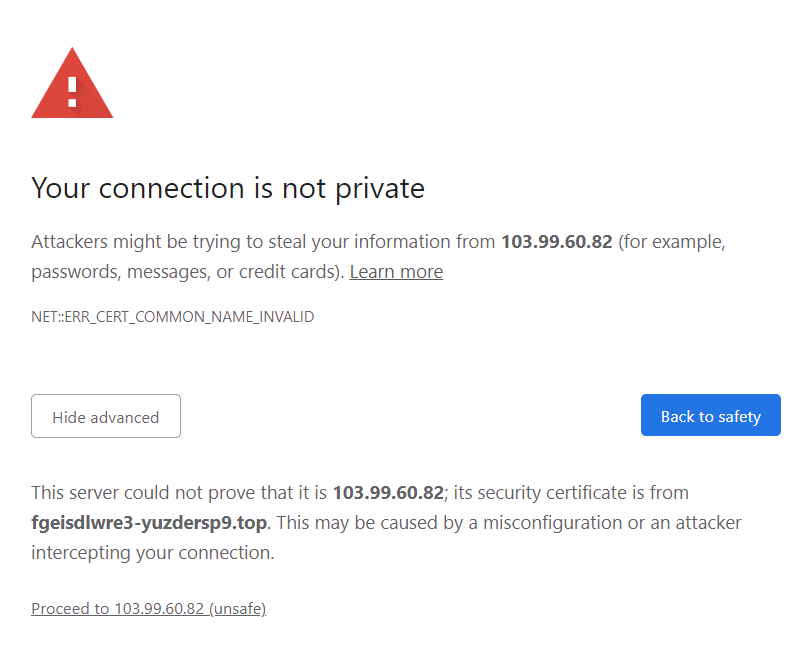
If we ignore the warning and proceed, we are directed to “https://fgeisdlwre3-yuzdersp9.top“. The domain loads yet another WordPress website, this time for the “Deluxe Home” brand which supposedly sells furniture.
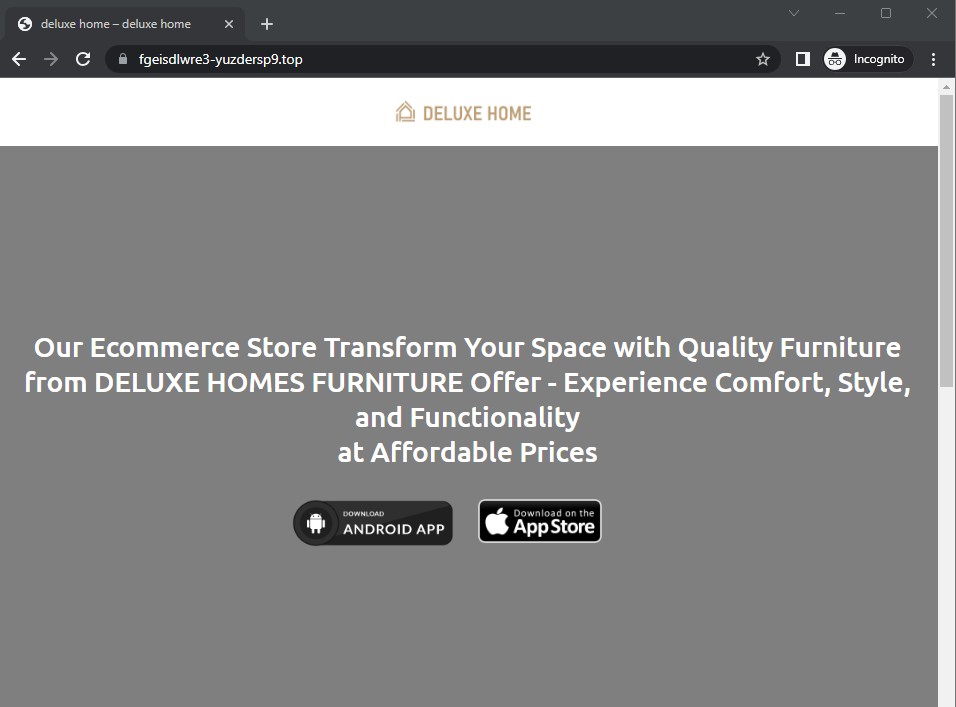
The site layout looks similar to our “1st Mall” sites and contains a download link to “Deluxe Home v3.0.apk“.
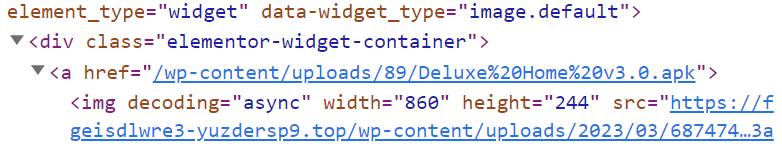
Interestingly, this “Deluxe Home” APK was not seen in the first section of this post and is very likely another scam series being operated.
Our journey thus far
Before we really go into the thick of it, let’s pause and visualize our journey thus far. Take some time to review the flowchart below to jog your memory.
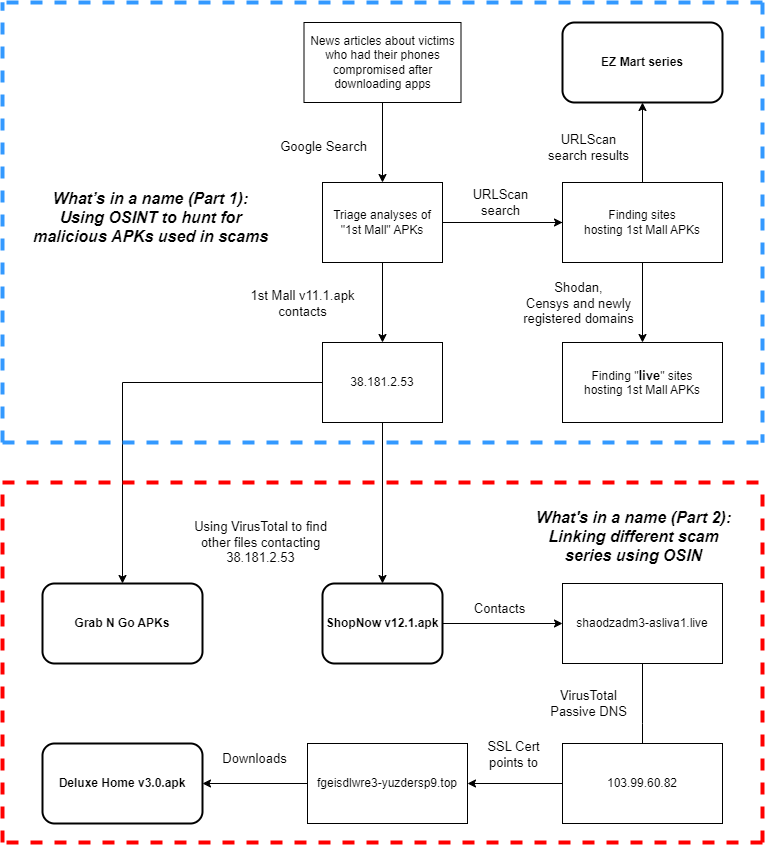
From the flowchart above, we see that we have uncovered at least 4 scam series so far. All of this started with a simple news article coupled with some quick OSINT work! That said, in any OSINT investigation, it is very easy to lose track of how you derived your findings, so ensure that your methods are verifiable.
Harnessing the power of VirusTotal
In this final section of the post, I will use VirusTotal’s graph and search functions to organize our findings, and show how far OSINT with VirusTotal can get us.
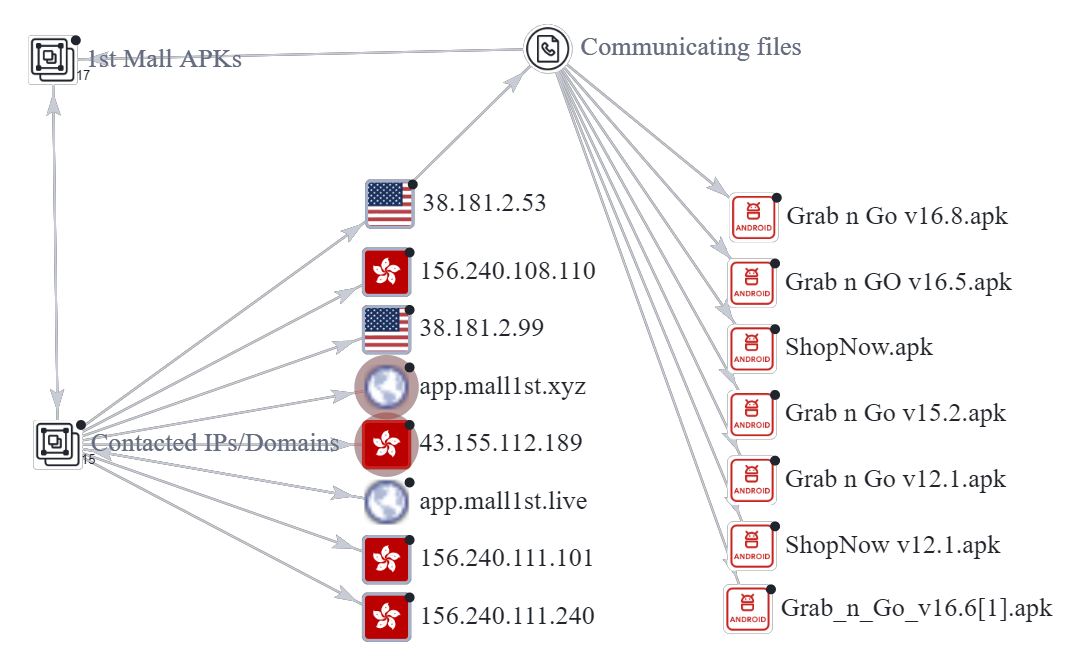
I started by plotting all the “1st Mall” APKs found in our previous post, and the relevant IP addresses/domains contacted by each APK. We see some overlaps in the contacted IP addresses and domains, similar to what we identified in our previous post.
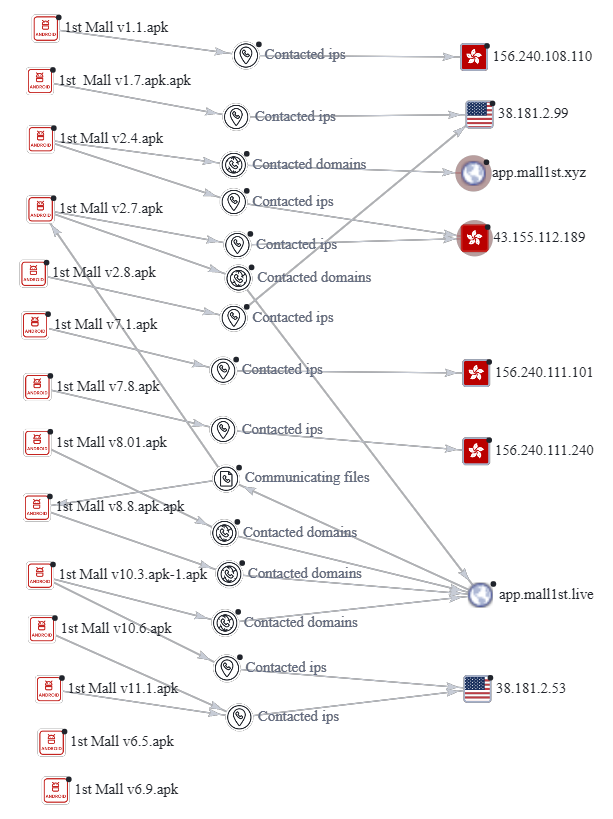
You can use the “Group Nodes” feature to combine the nodes into a group to organize the graph.
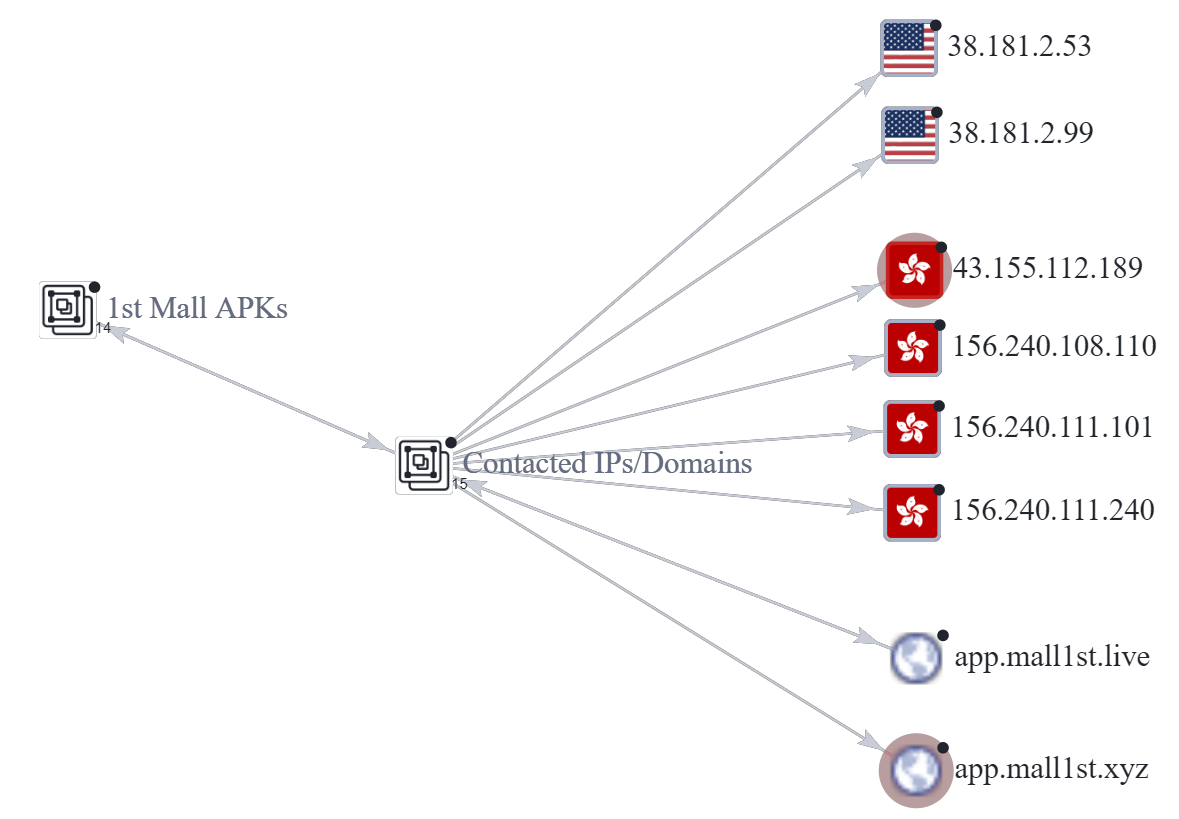
Next, we plot the files connecting to the IP address “38.181.2.53“. This reveals 3 more “1st Mall” APKs that we add to our grouped nodes, bringing the total number of “1st Mall” APKs to 17.
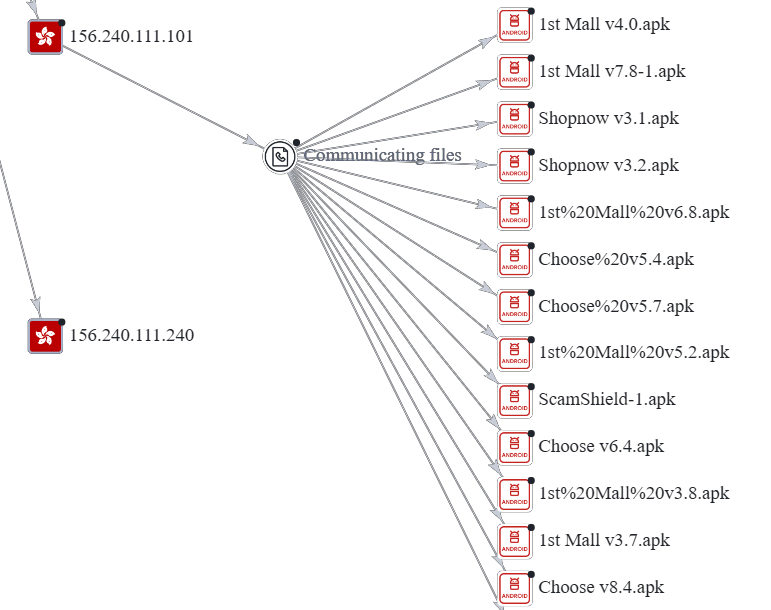
We repeat the process with the rest of the IP addresses, plotting files that contacted those IP addresses. In doing so, we find even more APKs fitting our naming convention from potential scam series that we not seen yet. For example, there were a few APKs named “Choose” and “ScamShield” (ScamShield is an anti-scam product developed by Singapore’s National Crime Prevention Council and Open Government Products).
The result of this process can be seen in the VirusTotal graph below:
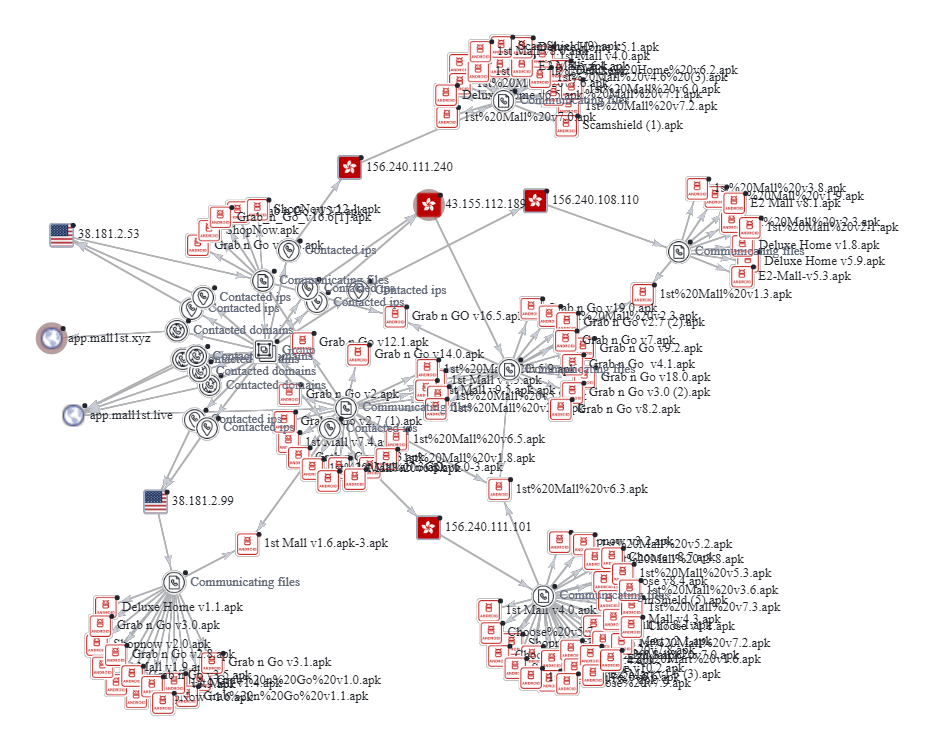
I also plotted the IP addresses of the servers hosting the “1st Mall” scam sites found in our previous post. Using VirusTotal’s “Passive DNS” resolutions, we found 275 sites potentially hosting the APKs we found above. The graph can be found here.
In total, we found 117 APKs across 7 different scam series – the breakdown of the files are as follows:
- 60 1st Mall
- 25 Grab n Go
- 6 ShopNow
- 6 Deluxe Home
- 5 ScamShield
- 6 Ez Mall
- 9 Choose
Key takeaways
Before we end off, here are some key takeaways from the two posts:
Size and experience of scam operators’ group
It is clear that the operators of the various scam series did not focus on only one series at a time. This is observed from the following points:
- Overlapping compiled dates of APKs
- Sheer volume of domains registered to host APKs
- Overlapping registration date of domains across different scam series
- Different versions of APKs from different scam series connecting to the same C2 servers
- No indication of slowdown in activity despite media coverage on scam series
These points speak to the size and experience of the scam operators’ group, suggesting that this is definitely not their first attempt at running scam operations.
Use of legitimate hosting service providers
There is little variance in the hosting providers used by the operators to host the domains and C2 servers. The operators tended to use hosting service providers based in Asia. While the exact reason for this is not known, it could be to bypass geolocation-based security measures or for the sake of familiarity to the operators.
Effectiveness of the Spynote malware family
Even though reports of the Spynote malware family can be found dating back to 2019, it is obvious that the malware is just as effective in achieving the operator(s) aims. Readers should be wary of downloading external applications from third-party sites and more so if the applications request for excessive permissions.
Final Words
From our two posts, we found several scam series believed to be run by the same operator(s). These scam series rely on malicious APKs from the spynote malware family to control victim devices with the aim of compromising bank accounts. These malicious APKs were merely rebranded to different themes but were ultimately similar in contents and served the same purpose, which really begs the question: Whats in a name?
Leave a Reply